IPv4数据包构造
根据IP地址构造
netwox工具提供编号为38的模块,用来构造IP数据包。用户不仅可以设置源IP地址和目标IP地址,还可以设置TTL、数据分片等字段。
(1) 不指定选项运行
执行命令如下:
C:\Program Files (x86)\netw\netw539>netwox 38
IP______________________________________________________________.
|version| ihl | tos | totlen |
|___4___|___5___|____0x00=0_____|___________0x0014=20___________|
| id |r|D|M| offsetfrag |
|_________0xB4EE=46318__________|0|0|0|________0x0000=0_________|
| ttl | protocol | checksum |
|____0x00=0_____|____0x00=0_____|____________0x38DA_____________|
| source |
|_________________________192.168.0.108_________________________|
| destination |
|____________________________5.6.7.8____________________________|
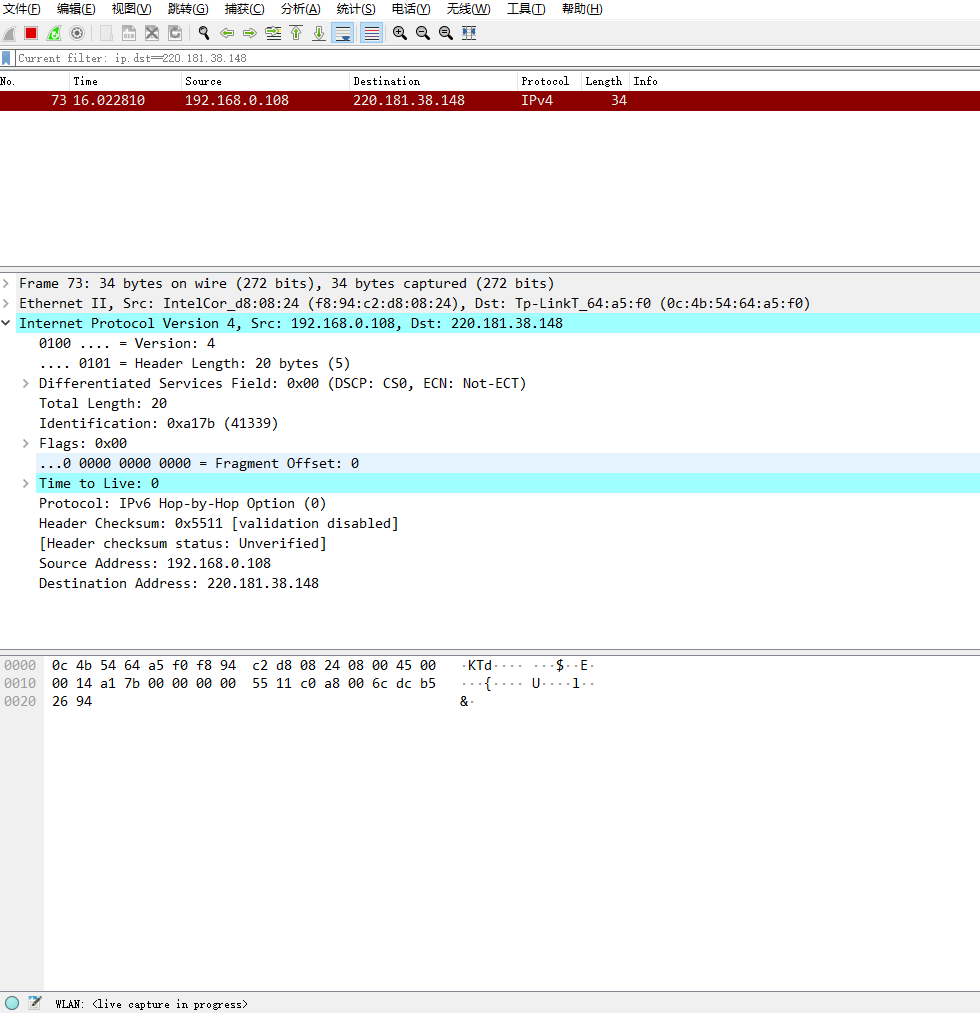
在输出信息中,第一行IP表示当前数据包是基于IP协议的。包中的字段值均为默认值。例如,源IP地址为192.168.0.108,目的IP地址为5.6.7.8。
(2) 指定源目IP地址
执行命令如下:
C:\Program Files (x86)\netw\netw539>netwox 38 -l 192.168.0.132 -m 192.168.10.101
IP______________________________________________________________.
|version| ihl | tos | totlen |
|___4___|___5___|____0x00=0_____|___________0x0014=20___________|
| id |r|D|M| offsetfrag |
|_________0xFD3E=64830__________|0|0|0|________0x0000=0_________|
| ttl | protocol | checksum |
|____0x00=0_____|____0x00=0_____|____________0x3172_____________|
| source |
|_________________________192.168.0.132_________________________|
| destination |
|________________________192.168.10.101_________________________|
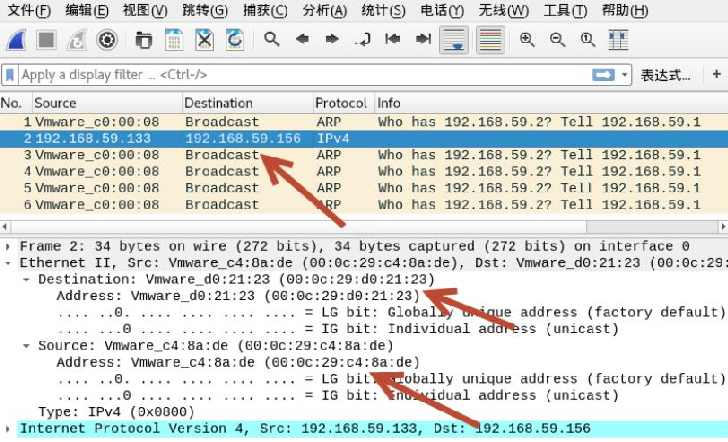
(3) 抓包验证构造的IP数据包
根据MAC地址构造
netwox工具提供编号为34的模块,用于指定IP数据报的以太层字段信息。
(1) 不指定选项,直接运行该模块,查看默认设置
执行命令如下:
C:\Program Files (x86)\netw\netw539>netwox 34
Ethernet________________________________________________________.
| F8:94:C2:D8:08:28->00:08:09:0A:0B:0C type:0x0800 |
|_______________________________________________________________|
IP______________________________________________________________.
|version| ihl | tos | totlen |
|___4___|___5___|____0x00=0_____|___________0x0014=20___________|
| id |r|D|M| offsetfrag |
|_________0x6D05=27909__________|0|0|0|________0x0000=0_________|
| ttl | protocol | checksum |
|____0x00=0_____|____0x00=0_____|____________0x80C3_____________|
| source |
|_________________________192.168.0.108_________________________|
| destination |
|____________________________5.6.7.8____________________________|
在输出信息中,第一行Ethernet表示当前数据包的以太网层字段信息。这些字段值均为默认值。例如,当前以太网的源MAC地址为F8:94:C2:D8:08:28,目标MAC地址为00:08:09:0A:0B:0C。
(2) 指定以太网的源MAC地址和目标MAC地址
执行命令如下:
C:\Program Files (x86)\netw\netw539>netwox 34 -a 00:0C:29:C4:8A:DE -b 00:0C:29:D0:21:23
输出信息如下:
Ethernet________________________________________________________.
| 00:0C:29:C4:8A:DE->00:0C:29:D0:21:23 type:0x0800 |
|_______________________________________________________________ |
IP______________________________________________________________.
|version| ihl | tos | totlen |
|___4___|___5___|____0x00=0_____|___________0x0014=20___________ |
| id |r|D|M| offsetfrag |
|_________0x6983=27011__________|0|0|0|________0x0000=0_________ |
| ttl | protocol | checksum |
|____0x00=0_____|____0x00=0_____|____________0x492E_____________ |
| source |
|____________________________192.168.59.131_________________________ |
| destination |
|____________________________192.168.59.156__________________________|
(3) 验证构造的数据包,使用Wireshark工具捕获数据包